Connecting an AzureAD SAML provider
by Sebastien Mirolo on Wed, 16 Nov 2022
 In this post we will delegate user authentication
for a Djaoapp-powered
Software-as-Service (SaaS) product to a SAML provider hosted by AzureAD.
In this post we will delegate user authentication
for a Djaoapp-powered
Software-as-Service (SaaS) product to a SAML provider hosted by AzureAD.
Creating Azure accounts
Reading through Azure documentation and understanding what needs to be done when you don't have prior Microsoft-specific historical knowledge can be quite difficult. One of the first thing we learned is we really need to create two Azure accounts in order to do any meanningful testing, one we will label provider and one we will label client. The provider will refer to our own SaaS product while the client account will refer to subscribers/users of our SaaS product.
Creating an account on Azure is actually tricky. In most cases it will require you to create a Microsoft-owned e-mail address. Fortunately we can sign in with GitHub credentials, so we will try that. After a couple redirects between GitHub and Azure, we use the work e-mail address for the provider and the personal @gmail e-mail address for the client.
Of course we get a cryptic error. That's typical of Microsoft OAuth workflow.
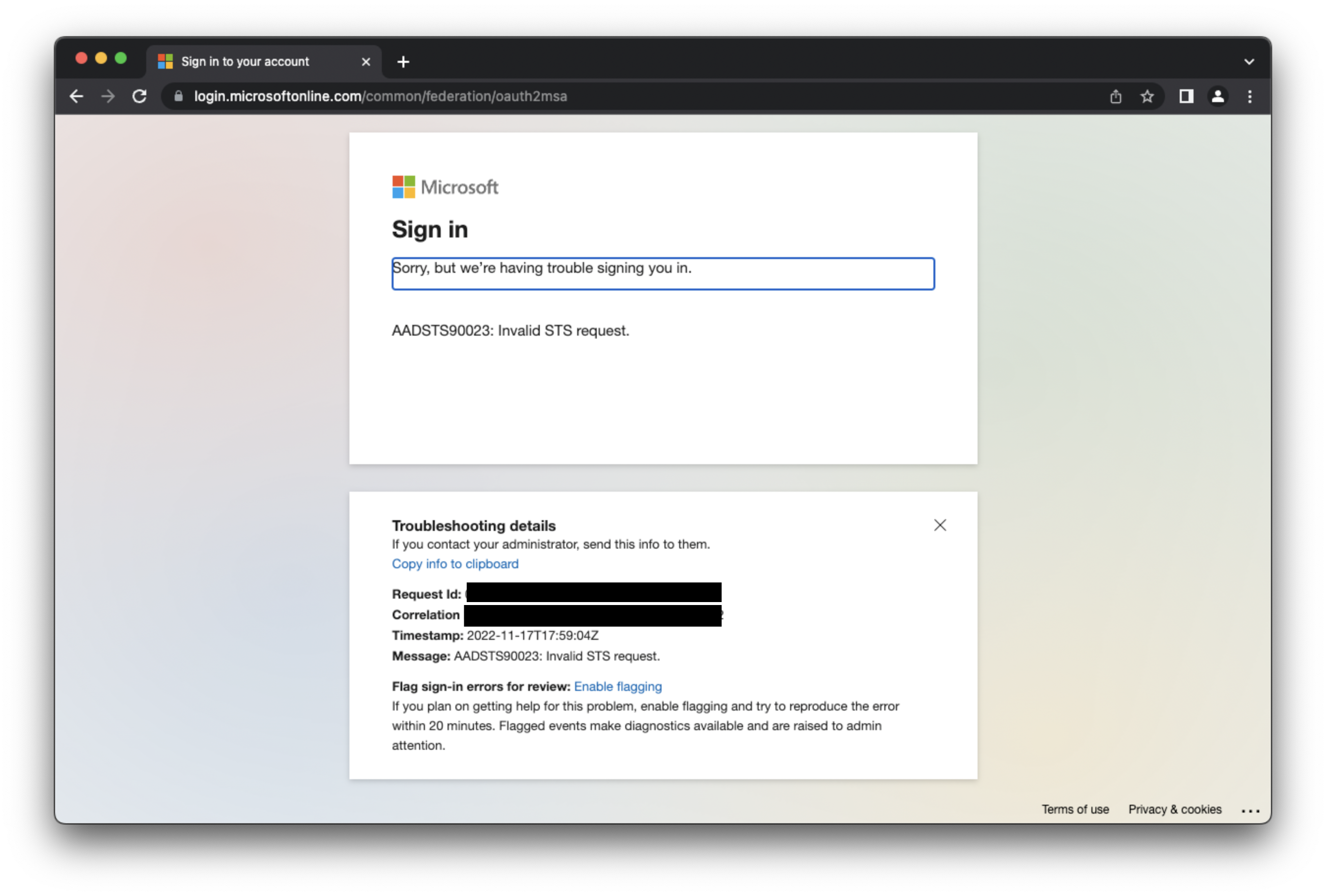
We go through the sign-in process again, receive a code to verify the @gmail.com address and end-up to the following screen.
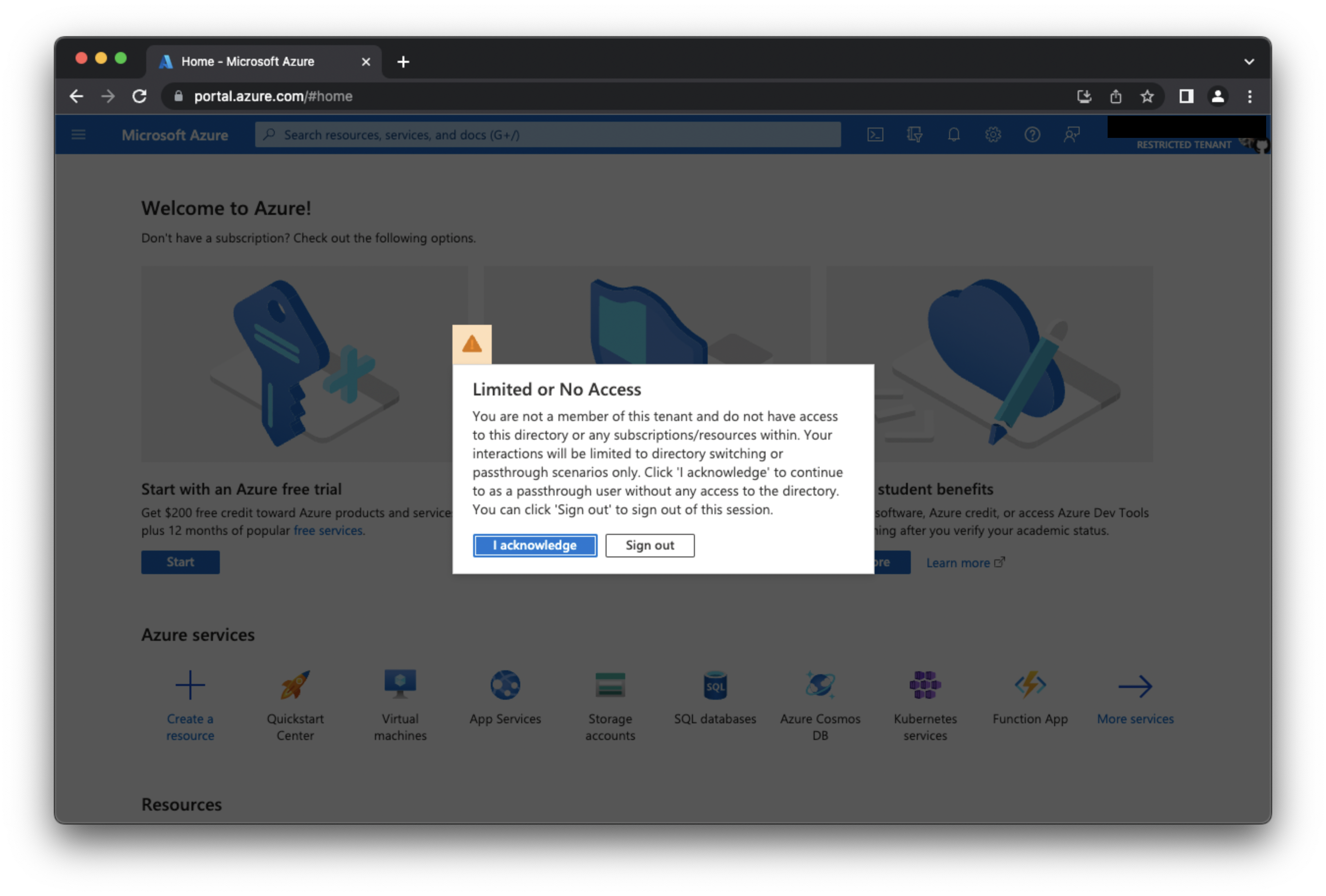
I have no idea what any of this means except somehow some things might not work - because I am using a @gmail.com e-mail address?
First, find a way to go to Azure Active Directory but end up on a permission error.
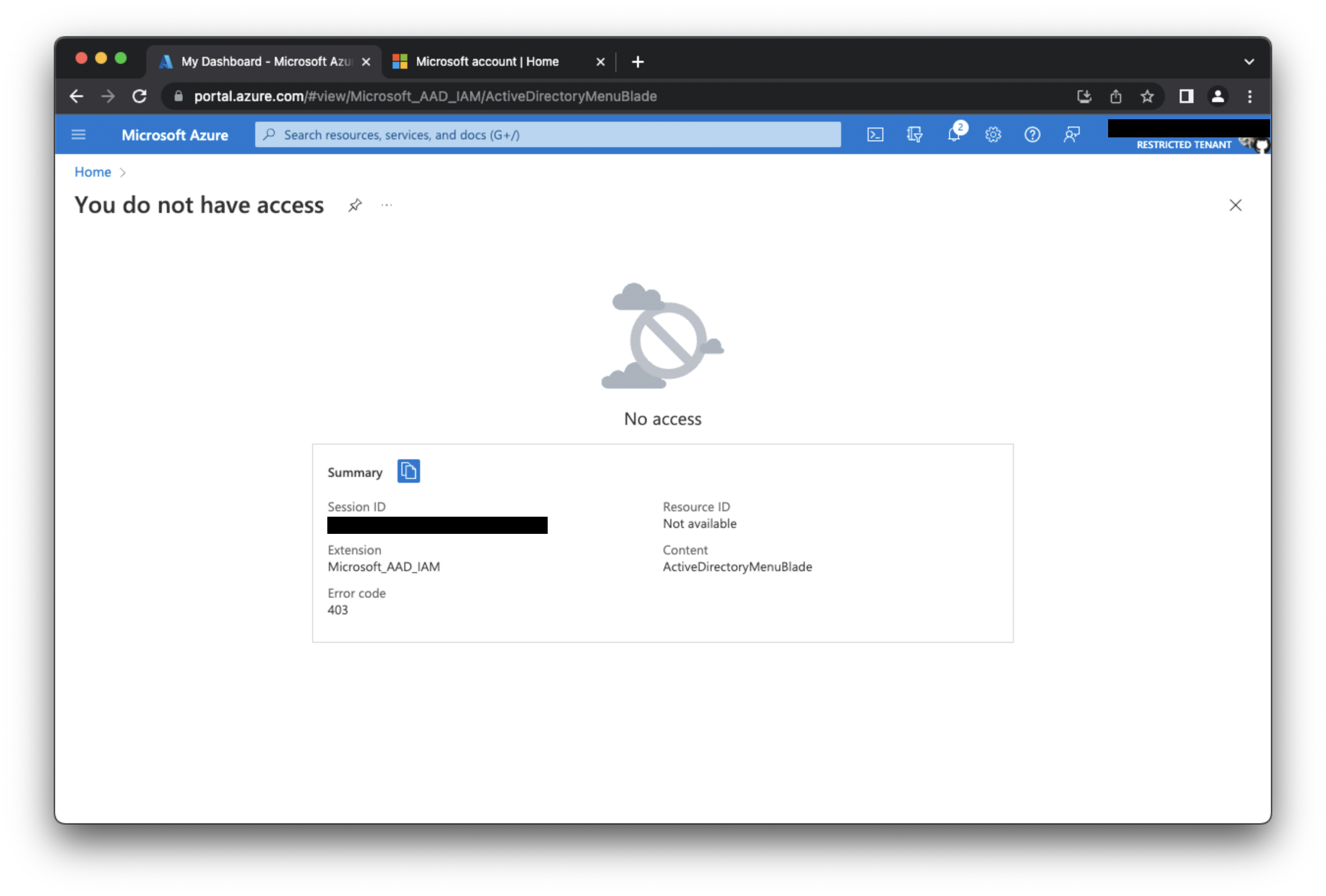
So we are back where we started. We clear the browser cache, go back to Azure Cloud, click Free account > Start free, then on the sign-in page we are greeted with a "No account? Create one!". The create account form is asking for an e-mail address so we will try our @gmail.com e-mail address again here. Now it says our @gmail.com e-mail is already a Microsoft account!
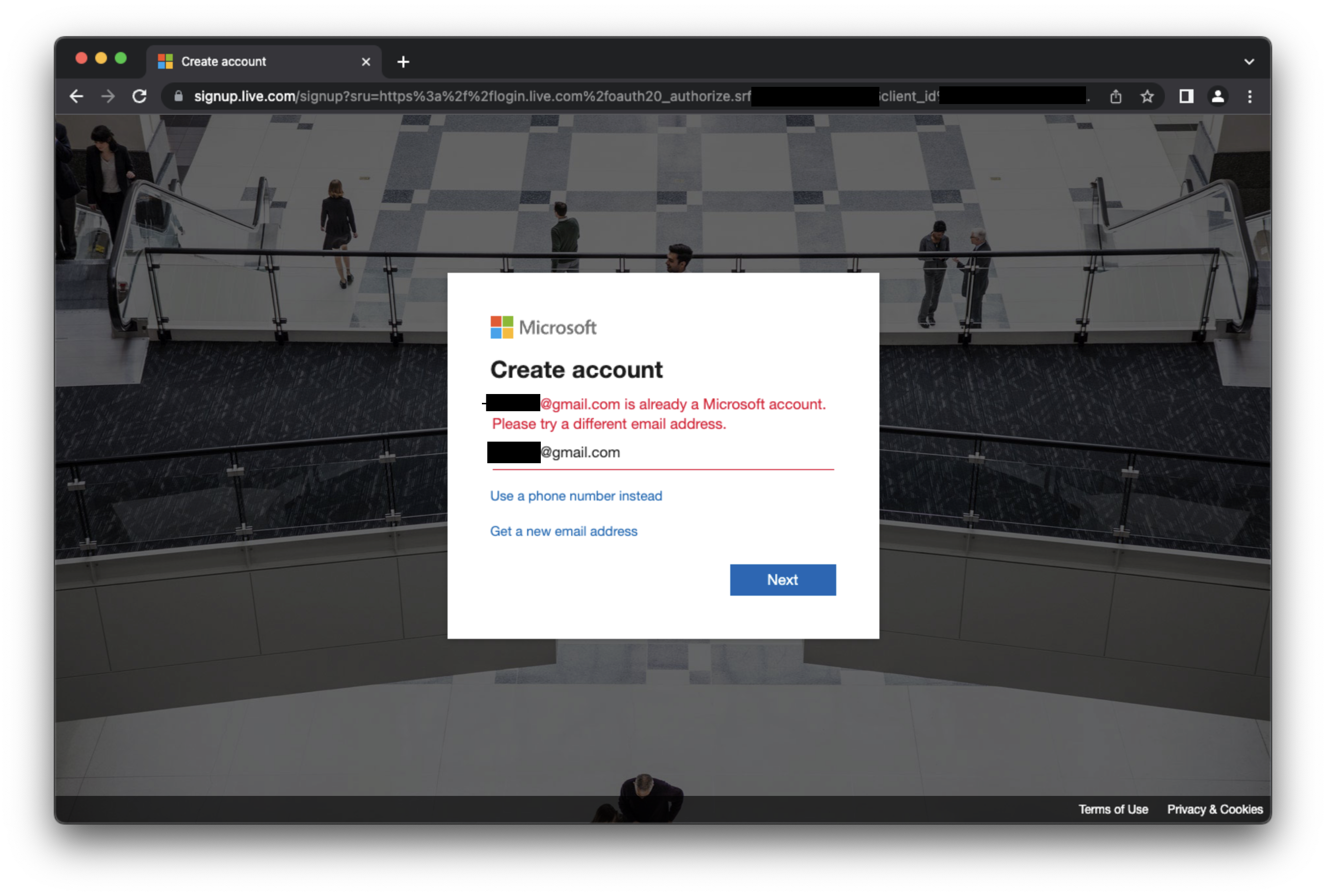
Let's try again. Go to Azure Cloud, click Free account > Start free. We are back on Sign-in form. We enter the @gmail.com e-mail address. This time that redirects us to GitHub where we enter the email address again, and the password.
This time through the various redirects we end-up on the Azure signup page!
I can enter a different e-mail address on the signup form but I would not dare here. After verifying phone number, we have to enter a credit card and click sign-up. There is a satisfaction survey passing through but by the time I write down this note, it disappears and shows a "You're not eligible for an Azure free account" message.
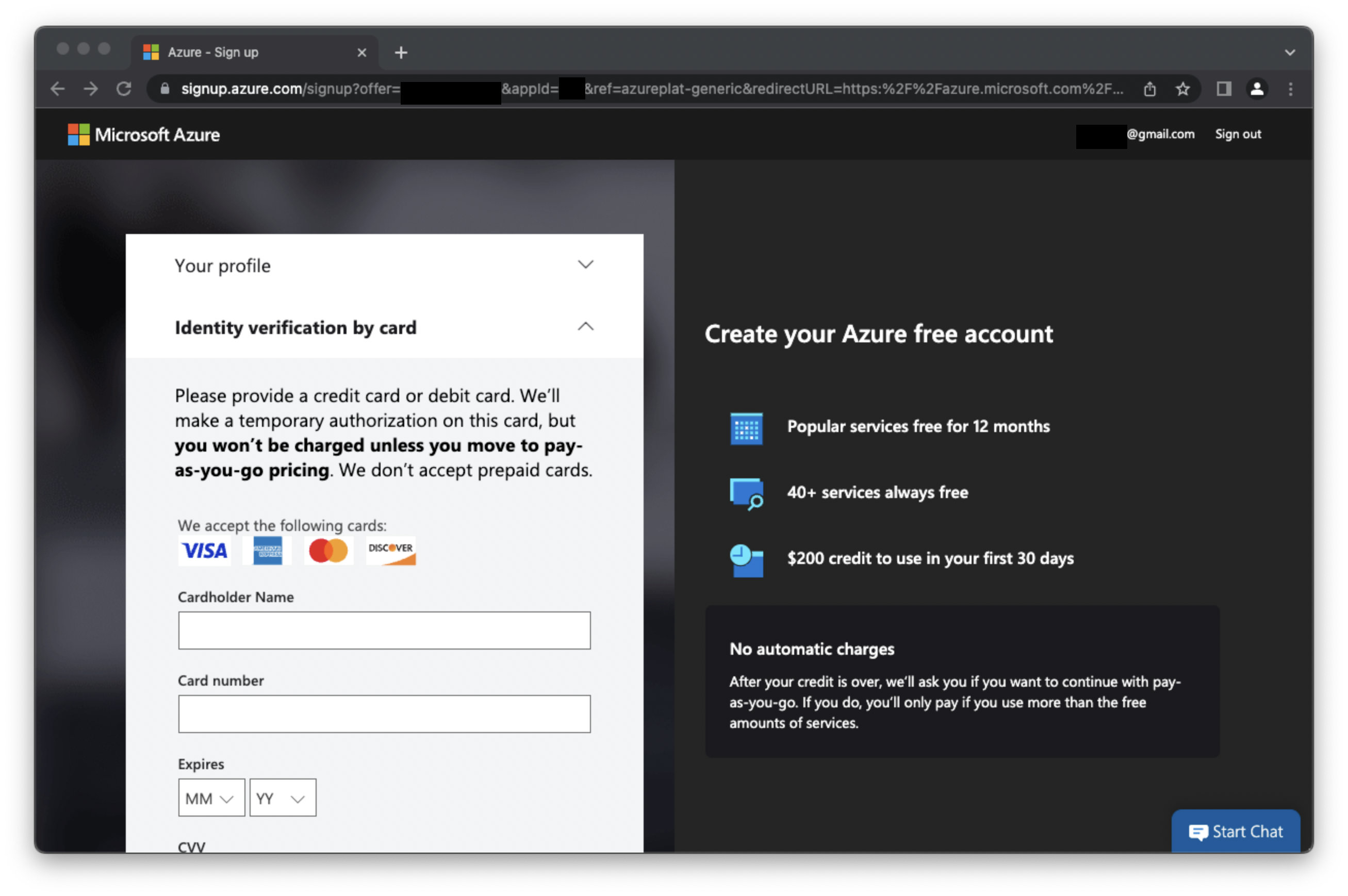
Click ok for signup-as-you go and back on the signup page. Under Add technical support I select "No technical support, or I am already covered through Microsoft Premier support." whatever that means.
"Are you satisfied ..." shows back up but again disapears before I have a chance to take notes and answer. At least it seems we are on the dashboard, no restriction this time!
AzureAD Configuration
We navigate to Azure Active Directory > Enterprise Applications, then click New Application followed by Create your own application.
We go through the creation wizard.
- What's the name of your app?
- Name
- What are you looking to do with your application?
- Integrate any other application you don't find in the gallery (Non-gallery)
Click Single sign-on in the left side menubar, then click on SAML.
On the SAML page, click Upload metadata file at the top and upload the file that was generated by the application (i.e. https://domain/saml/)
We also populate the various redirects.
- Sign on URL
- https://domain/login/
- Relay State
- https://domain/complete/saml/
- Logout Url
- https://domain/logout/
DjaoApp Configuration
We then add an entry in djaoapp settings.py with the information provided by AzureAD.
SOCIAL_AUTH_SAML_ENABLED_IDPS = {
"example.com": {
"entity_id": "https://sts.windows.net/tenant_id/
"url": "https://login.microsoftonline.com/tenant_id/saml2",
"x509cert": "...",
"attr_user_permanent_id": "user.userprincipalname",
"attr_email": "user.mail",
"attr_first_name": "user.givenname",
"attr_last_name": "user.surname"
}
Finally we update the djaoapp database to redirect all attempts to sign up, or login with an @example.com e-mail address to the SAML workflow.
$ psql -c "INSERT INTO signup_delegateauth (domain, provider) VALUES ('example.com', 'saml');" db_name
Allowing AzureAD users to access the SaaS product
Now that we have connected our DjaoApp-powered SaaS product with AzureAD, we need to assign users on AzureAD allowed to access our SaaS product.
Click Users and groups, then Add user/group.
